How Malware attack and their types
In this age of Artificial Intelligence we are surrounded by machines,in fact we are dependent on machines everything is computerized our banking system everything !!
It is also believed that a cyber attack can cause complete financial damage to a country.It is more dangerous than a nuclear weapon.So here I am going to discuss different types of Malwares and how they attack
Types of Malware
1.Virus:
Viruses basically attach itself to a software or application and when we download that software from internet and use that software it gets active.If we don't use that software which has virus it does not get active.A virus can not spread without a human action
How virus works:
CACHE --> contains frequently used data which we need later for use.
RAM --> It works while PC is powered on and contains our OS and currently running applications.In fact anything which need to be run is put on RAM from hard disk.
IP REGISTER --> contains address of next instruction.
CU(CONTROL UNIT) --> It execute next instruction on IP register.
It appears to be useful but contains hidden programs. It comes in shape of normal application.It allows hackers gain full access of system.
Scenario:
Suppose we downloaded one software but another unknown software start to download automatically which we don't want.It opens backdoor and credential information to hackers.
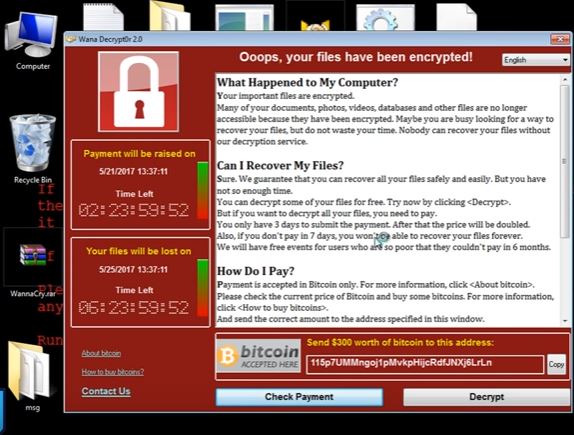
4.Ransomware
It is also an unwanted software which is automatically downloaded on your system which is send through email or comes with cracked software downloaded from torrent or any other source.That software encrypts your hard disk files by using cryptography which locks your system files and demand you to pay payment to hacker in bitcoins and after that he will provide you the decryption key which will unlock your system files.
5.Rootkits
If this software which is actually a malware if installed on your system it gain root access of your system which remain hidden and continues to perform its activities without knowing . It comes in many modes two of them are user mode and system mode.
User mode:It does not harm much because in this mode it is not given direct privilege of the system hardware.
System mode: It gives direct access privilege of system hardware.It is very dangerous as it can't be detected because operating system understand it as part of the system
Firmware:It hides in firmware because firmware is usually not inspected and change system settings of BIOS
Working
CU normally execute next instruction on IP register i.e Instruction 1 at address 100 .Now when the virus gets active it changes value on IP register for example CU is executing Instruction 2 at address 101 but virus changes the address value to 1000 which contains virus and now virus is loaded on RAM and your computer gets infected.
2.WORMS :
It has a characteristic of self replication (It can transfer itself from one computer to many other computers without a human action). Due to its characteristic of copying itself it slows down the system or network because all resources(RAM,CPU,Bandwidth etc)are used by worms.
If your computer has a worm then your computer can be converted into botnet and used by hacker to do Denial of service attack(DDOS) attack.
If your computer has a worm then your computer can be converted into botnet and used by hacker to do Denial of service attack(DDOS) attack.
It appears to be useful but contains hidden programs. It comes in shape of normal application.It allows hackers gain full access of system.
Scenario:
Suppose we downloaded one software but another unknown software start to download automatically which we don't want.It opens backdoor and credential information to hackers.
4.Ransomware
It is also an unwanted software which is automatically downloaded on your system which is send through email or comes with cracked software downloaded from torrent or any other source.That software encrypts your hard disk files by using cryptography which locks your system files and demand you to pay payment to hacker in bitcoins and after that he will provide you the decryption key which will unlock your system files.
5.Rootkits
If this software which is actually a malware if installed on your system it gain root access of your system which remain hidden and continues to perform its activities without knowing . It comes in many modes two of them are user mode and system mode.
User mode:It does not harm much because in this mode it is not given direct privilege of the system hardware.
System mode: It gives direct access privilege of system hardware.It is very dangerous as it can't be detected because operating system understand it as part of the system
Firmware:It hides in firmware because firmware is usually not inspected and change system settings of BIOS









No comments